In an increasingly digital world, cybersecurity remains a paramount concern for organizations in every sector. As cyberattacks grow more frequent and complex, governments and regulatory bodies worldwide are implementing stricter frameworks to safeguard sensitive information, protect consumer privacy, and defend critical infrastructure. While these measures are essential for national and global security, they also introduce complex obligations for businesses. Companies must adapt to this shifting landscape by implementing more robust security measures, investing in technologies, and managing compliance on both national and international scales.
This article explores the most recent changes in international cybersecurity regulations, outlines the challenges and opportunities they bring to organizations in various industries, and provides best practice recommendations for staying ahead in this dynamic environment.
The Growing Need for Cybersecurity Regulation
Global cybercrime costs are forecasted to reach $10.5 trillion annually by the end of 2025. The alarming surge in data breaches, ransomware campaigns, supply chain attacks, and phishing exploits has exposed major vulnerabilities in both private and public sector infrastructure. High-profile incidents involving healthcare providers, financial institutions, energy grids, and government databases have prompted an unprecedented regulatory response.
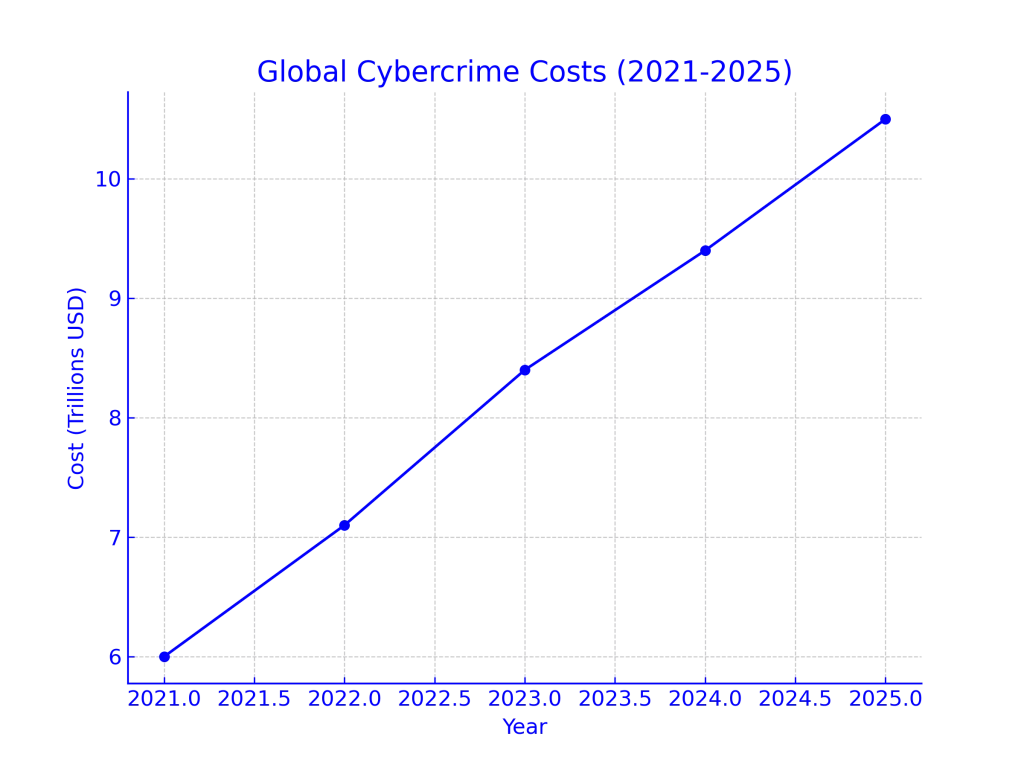
Governments are acting to impose stricter oversight, mandating that businesses implement comprehensive cybersecurity frameworks. The goal is to standardize security practices, promote accountability, and encourage cross-border collaboration. Yet, with differing national laws, cultural considerations, and economic priorities, businesses face the daunting challenge of navigating a fragmented regulatory environment. Key regulatory efforts have emerged from the European Union, the United States, Asia-Pacific nations, and international standards organizations, each bringing its unique perspective and requirements.
Recent Updates in International Cybersecurity Regulations
European Union: Full Implementation of the NIS2 Directive
The European Union’s NIS2 Directive came into effect in late 2024, replacing the original NIS Directive. NIS2 expands its scope to cover more sectors, including digital infrastructure providers, postal and courier services, and waste and water management. It strengthens security requirements for both essential and important entities across critical sectors.
The Directive imposes stringent obligations for incident reporting, with organizations now required to report significant cyber incidents within 24 hours of detection. It mandates a holistic risk management approach, including internal policies for information system security, business continuity planning, and supply chain security. Financial penalties for non-compliance are substantial, reaching up to €10 million or 2% of global annual turnover, whichever is higher.
For businesses, this means rigorous third-party risk assessments, security audits, and employee awareness training programs have become necessary parts of operational resilience strategies.
United States: Expanded Federal Cybersecurity Mandates
The U.S. federal government has continued to tighten cybersecurity standards. A major executive order issued in early 2025 mandates the establishment of minimum cybersecurity requirements for all federal contractors and technology vendors. The order introduces a formal Cyber Trust Label for internet-connected devices and requires all contractors to provide evidence of continuous compliance.
Additionally, the U.S. Securities and Exchange Commission has finalized rules mandating public companies to disclose material cybersecurity incidents within four business days. The order also calls for improvements in securing the nation’s critical infrastructure, including energy, transportation, financial services, and telecommunications, while explicitly recognizing the potential threats posed by quantum computing and emerging AI technologies.
Sector-specific regulations have also been strengthened. Healthcare organizations face updated HIPAA guidelines that expand breach notification requirements and emphasize multi-layered defense models against ransomware. The financial sector remains tightly regulated under frameworks such as GLBA and the updated cybersecurity risk management proposals from the Federal Reserve and the Office of the Comptroller of the Currency.
Asia-Pacific: Strengthened Cybersecurity Regulations
Singapore remains a leader in cybersecurity regulation in the Asia-Pacific region. Amendments to the nation’s Cybersecurity Act, passed in 2024, expanded its regulatory reach beyond Critical Information Infrastructure (CII) sectors to include system owners operating systems of significant importance. These amendments increase the Cyber Security Agency of Singapore’s enforcement powers, introduce tiered fines for non-compliance, and require organizations to conduct regular cybersecurity assessments and submit vulnerability reports.
Elsewhere in Asia-Pacific, Japan’s Basic Act on Cybersecurity has continued evolving to address the growing threat landscape, incorporating specific measures for securing IoT ecosystems and mitigating AI-powered cyber risks. Australia’s Security of Critical Infrastructure Act (SOCI) also expanded to include cloud service providers, data storage operators, and critical logistics providers. The Act now requires regulated entities to notify authorities of cyber incidents within 72 hours and to proactively submit detailed risk management plans.
Global Standards: ISO and NIST Framework Enhancements
The International Organization for Standardization published the revised ISO/IEC 27001:2022 standard, with a transition deadline set for late 2025. The update introduces enhanced controls focusing on cloud security, supply chain security, remote work, and zero-trust architecture principles. Organizations certified under older versions are actively transitioning to meet the new requirements.
In the United States, the National Institute of Standards and Technology (NIST) finalized Cybersecurity Framework (CSF) 2.0. The revised framework introduced a sixth core function, “Govern,” aimed at emphasizing executive accountability and governance over cybersecurity risk. CSF 2.0 provides clearer guidance for organizations of all sizes to assess, manage, and communicate cybersecurity risks, especially in the context of rapidly evolving threats and global supply chains.
Impact on Businesses Across Sectors
Technology and Software
Technology companies that collect, process, and store large volumes of personal data remain under intense regulatory scrutiny. Compliance with GDPR, CCPA, and the latest U.S. federal mandates requires substantial investments in privacy engineering, encryption, and secure development practices. Many firms are now adopting privacy-by-design and security-by-default models to reduce regulatory risk.
Healthcare
Healthcare providers and life sciences companies face particularly severe consequences from cyber incidents. Regulatory bodies have responded by mandating tighter controls on medical devices, electronic health records, and connected healthcare systems. The industry is also under increasing pressure to implement continuous monitoring and to document robust incident response plans.
Financial Services
The financial sector remains one of the most heavily regulated industries for cybersecurity. Regulators require regular stress testing of systems, multi-factor authentication for customer access, and continuous threat intelligence monitoring. New rules in 2025 have made it mandatory for publicly traded companies to maintain detailed cyber risk governance disclosures and to swiftly inform regulators of material incidents.
Manufacturing and Critical Infrastructure
Critical infrastructure operators face mounting threats from state-sponsored attackers and ransomware groups. The latest regulations impose mandatory penetration testing, segmentation of operational technology (OT) networks, and heightened collaboration with national security agencies. The increased focus on ICS and SCADA system security has resulted in significant capital expenditures for compliance.
Retail and E-Commerce
Retailers and e-commerce platforms must navigate complex data privacy laws and payment security standards. Compliance requires continual updating of AI-driven fraud detection systems and secure payment gateway technologies. Retailers must also adhere to breach notification laws that vary widely across jurisdictions.
Compliance Challenges
The sheer volume and diversity of cybersecurity regulations present enormous challenges for businesses:
- Cost and Complexity: SMEs often lack the financial and human resources to implement all the necessary compliance programs.
- Global Talent Shortage: There is a persistent shortage of qualified cybersecurity professionals, intensifying competition for talent.
- Emerging Threats: Rapidly developing technologies, such as generative AI and quantum computing, continue to outpace regulatory frameworks, exposing businesses to unforeseen risks.
- Data Transfer Restrictions: The lack of uniform global data transfer agreements complicates cross-border operations, with the EU and U.S. still ironing out legal solutions post-Privacy Shield.
Compliance Opportunities
Despite the burdens, regulatory changes also offer strategic benefits:
- Innovation: Compliance drives advancements in cybersecurity technologies, such as zero-trust network access, advanced behavioral analytics, and blockchain-enabled data integrity tools.
- Competitive Edge: Organizations that lead on compliance and security posture gain trust, reduce reputational risks, and stand out in highly competitive markets.
- Collaboration and Resilience: Regulations are encouraging deeper partnerships between private companies, regulators, and law enforcement, enhancing collective cyber resilience across entire industries.
Best Practices for Navigating Regulatory Compliance
To succeed in this complex landscape, businesses should prioritize:
- Regular, proactive risk assessments of internal and third-party systems.
- Organization-wide employee cybersecurity training programs.
- Deployment of cutting-edge tools for endpoint protection, network monitoring, and data loss prevention.
- Engagement with specialized legal and compliance experts to track and interpret new regulatory developments.
- Development and routine testing of incident response and recovery plans.
The Future of Cybersecurity Regulation
Key trends expected to dominate the next wave of cybersecurity regulations include:
- AI Regulation: Governments will increasingly regulate how artificial intelligence is deployed securely and ethically in critical sectors.
- Post-Quantum Cryptography: Global efforts will intensify to define standards for encryption resilient to quantum computing advances.
- Global Harmonization: There is rising momentum toward aligning cybersecurity standards across jurisdictions to ease compliance for multinational organizations.
- Data Sovereignty and Consumer Empowerment: Regulatory frameworks will continue to expand individual rights around data access, portability, and deletion.
Conclusion
The pace of regulatory change in cybersecurity shows no sign of slowing. While compliance is a costly and complex undertaking, it also presents opportunities for organizations to innovate, build resilience, and enhance customer trust. Businesses that stay informed, adapt proactively, and embrace strong governance frameworks will be well-positioned to thrive in the face of escalating cyber risks. The future of global commerce increasingly depends on cybersecurity being treated as both a legal requirement and a strategic business priority.
