No organization is immune to cyber threats. Whether you’re a financial institution, healthcare provider, government agency, or small business, the risk is real — and it’s growing. Cyberattacks are no longer rare, one-off incidents; they’re persistent, evolving, and increasingly damaging.
Traditionally, cybersecurity efforts have focused heavily on prevention. But in a world where breaches are inevitable, organizations must go a step further. They need to build cyber resilience — the ability to withstand, recover from, and adapt to cyber incidents, ensuring continuity and minimizing impact.
This article provides an in-depth look at how organizations can build a truly resilient cybersecurity posture, focusing on real-world strategies, incident response planning, and organizational preparedness.
What Is Cyber Resilience?
Cyber resilience is an organization’s capacity to prepare for, respond to, and recover from cyber threats and incidents without compromising core operations. It encompasses more than just blocking attacks — it’s about being able to bounce back quickly and maintain functionality, even when systems are under duress.
Think of it as the difference between putting up a strong wall (cybersecurity) and knowing how to survive a breach when the wall is breached (cyber resilience).
Why Cyber Resilience Matters Now More Than Ever
Cyber threats are escalating in frequency, severity, and complexity. The statistics paint a stark picture:
- The average cost of a data breach has surpassed $4 million globally.
- Over 70% of organizations report experiencing at least one security incident annually.
- The majority of breaches — over 80% — involve a human element, such as phishing or misconfiguration.
- Ransomware attacks are up year over year, often crippling operations for days or weeks.
- Downtime costs organizations thousands of dollars per minute — sometimes far more for critical sectors like healthcare or finance.
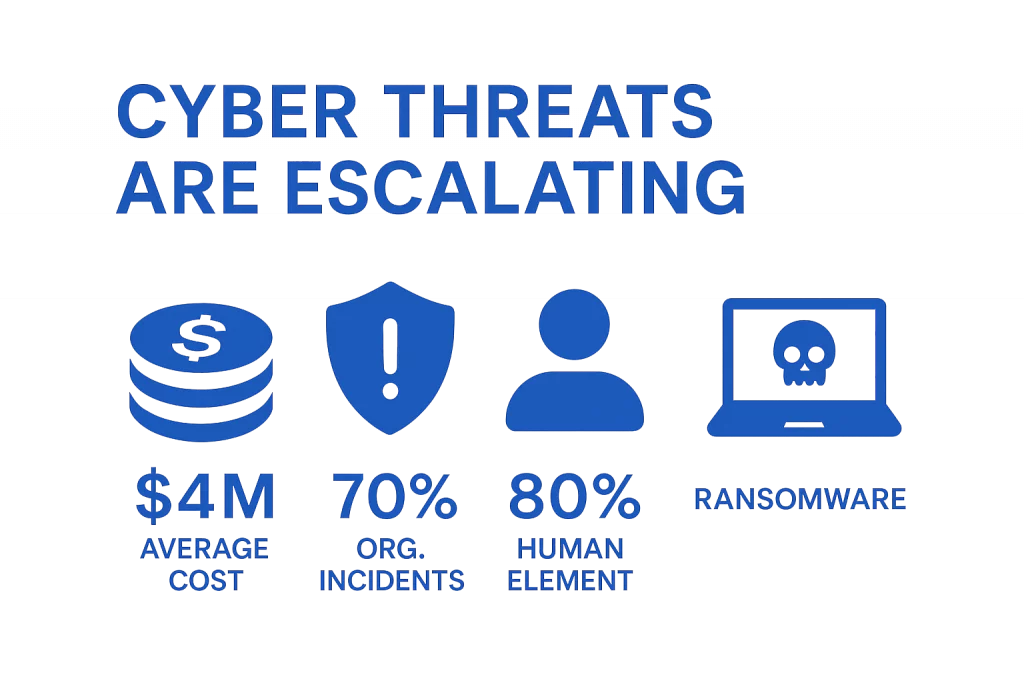
Simply put, organizations can no longer rely on prevention alone. The reality is that cyber incidents are inevitable, but a strong resilience strategy can mean the difference between a minor disruption and a full-scale crisis.
The Four Core Pillars of Cyber Resilience
A resilient organization isn’t one that avoids all attacks — it’s one that survives them. These are the four essential capabilities:
1. Anticipate
Proactively identifying risks before they become threats:
- Conduct regular risk assessments
- Maintain real-time threat awareness
- Identify critical assets and potential attack vectors
- Model cyber scenarios and business impact
2. Withstand
Building the ability to endure attacks with minimal disruption:
- Implement layered defense-in-depth security controls
- Apply Zero Trust principles, verifying all users and endpoints
- Ensure redundancy in infrastructure
- Train users to detect and report suspicious activity
3. Recover
Minimizing the damage and restoring normal operations quickly:
- Maintain secure, offline backups
- Develop and test disaster recovery and business continuity plans
- Prioritize system and data restoration
- Communicate clearly with internal and external stakeholders
4. Adapt
Improving continuously to become stronger after each event:
- Conduct post-incident reviews
- Update policies and controls based on new insights
- Evolve with the threat landscape and changing technologies
- Foster a learning culture and agility across teams
Strategic Approaches to Building Cyber Resilience
1. Create a Resilience Framework
Start with a formal structure to guide cyber preparedness:
- Establish clear governance and accountability
- Define risk appetite and tolerance levels
- Identify dependencies between systems, processes, and data
- Align resilience efforts with business objectives, not just IT goals
Frameworks should be tailored, scalable, and regularly updated to reflect organizational growth and emerging risks.
2. Integrate Cyber Risk Into Enterprise Risk Management
Cyber risk is business risk. It must be considered at the executive and board levels:
- Include cyber scenarios in risk portfolios
- Map cyber incidents to potential operational, reputational, and legal consequences
- Conduct simulations and tabletop exercises involving leadership
Decisions about cyber investments, insurance, and crisis response planning should be grounded in an understanding of organizational impact, not just technical threat models.
3. Build an Incident-Ready Culture
Culture is a critical, often overlooked element of resilience:
- Encourage transparency: early reporting is better than cover-ups
- Train staff regularly on phishing, secure communication, and data handling
- Empower employees with clear protocols during incidents
- Ensure cyber roles and responsibilities are understood across departments
People remain one of the most significant vulnerabilities — but they can also be one of the strongest assets when trained and engaged.
4. Secure the Entire Ecosystem
Your defenses are only as strong as your weakest link:
- Evaluate third-party vendors for cyber risks
- Include resilience requirements in contracts
- Ensure partner systems don’t introduce vulnerabilities
- Maintain visibility into third-party data access and activity
Supply chain attacks and service provider vulnerabilities are increasingly common — and devastating.
5. Invest in Detection, Automation, and Response
Even the best prevention tools can’t stop every attack. Speed matters:
- Implement centralized monitoring and event logging
- Use automation for incident triage and early containment
- Apply behavioral analytics to detect unusual activity
- Integrate threat detection with response playbooks
Quick detection and reaction reduce the “dwell time” — the period attackers are inside your system — which is critical for damage control.
The Role of an Incident Response Plan (IRP)
A comprehensive Incident Response Plan is at the heart of any resilience strategy. It’s the formal roadmap that guides the organization when responding to a cyber incident.
Key Elements of an Effective IRP:
- Preparation
- Define incident types and escalation protocols
- Establish a cross-functional incident response team
- Maintain updated contact lists and communication trees
- Ensure tools and forensic procedures are in place
- Define incident types and escalation protocols
- Identification
- Set thresholds for what qualifies as an incident
- Establish logging, alerting, and detection mechanisms
- Begin documentation and incident classification
- Set thresholds for what qualifies as an incident
- Containment
- Isolate affected systems or users
- Prevent lateral movement across networks
- Preserve evidence for legal and investigative purposes
- Isolate affected systems or users
- Eradication
- Remove malware or intruders
- Close exploited vulnerabilities
- Reset credentials and apply patches
- Remove malware or intruders
- Recovery
- Restore operations based on business priorities
- Validate integrity of restored systems
- Communicate recovery progress transparently
- Restore operations based on business priorities
- Post-Incident Review
- Conduct a root cause analysis
- Document lessons learned and gaps identified
- Update policies, playbooks, and training
- Conduct a root cause analysis
Regular testing of the IRP — through drills and tabletop exercises — is essential. An untested plan is no better than no plan at all.
How to Measure Cyber Resilience
You can’t improve what you don’t measure. Key performance indicators (KPIs) help organizations gauge resilience and improve over time.
Common Resilience Metrics:
- Mean Time to Detect (MTTD): How long it takes to identify a threat
- Mean Time to Respond (MTTR): How long it takes to contain and eliminate it
- Downtime Duration: Total time critical services are unavailable
- Recovery Point Objective (RPO): Acceptable data loss in terms of time
- Recovery Time Objective (RTO): Maximum acceptable time to resume service
- User Awareness Rates: Percent of staff passing security training or phishing tests
- Number of Incidents by Severity: Helps prioritize resources and controls
Tracking these metrics helps translate resilience from a concept to a measurable business value.
Conclusion: From Defense to Durability
The question organizations must ask today isn’t “How do we stop every attack?” but rather, “How do we keep going when one gets through?” The ability to recover, adapt, and maintain operations is what sets resilient organizations apart from vulnerable ones. Building cyber resilience is an ongoing journey. It requires leadership commitment, cross-functional collaboration, and a forward-looking mindset. The more resilient your organization becomes, the less power cyber adversaries hold — and the more confident your customers, partners, and employees can be in your stability and trustworthiness.
